Threat Intelligence in OpenWrt?!

In my previous post, I've showcased my initial setup for my GL.iNet Flint 3. Now I want to customize it further.
If you've expose port(s) to the internet before, then you know that there's a lot of malicious requests coming. These requests are normally target a known CVE and the attacker hopes that by scanning a large number of IPs and domains, they would catch a few vulnerable servers. For example, this is the log of my reverse proxy just now.
87.255.194.135 - - [19/Sep/2025:17:04:32 +0000] "GET /admin/config.php HTTP/1.0" 302 138 "-" "xfa1" "-"
87.255.194.135 - - [19/Sep/2025:17:51:21 +0000] "GET /admin/config.php HTTP/1.0" 400 248 "-" "xfa1" "-"
45.95.147.173 - - [19/Sep/2025:21:47:23 +0000] "CONNECT example.com:443 HTTP/1.1" 400 150 "-" "-" "-"
146.70.189.88 - - [19/Sep/2025:22:49:55 +0000] "GET /.git/config HTTP/1.1" 302 138 "-" "Mozilla/5.0 (compatible; Scanner/1.0)" "-"Honestly, I don't worry myself too much about these mass attacks. They are aiming for vulnerable software and I always update my software regularly. They are also not the kind of attacks that took much bandwidth like DDoS attacks. I think there no sure way to block these kind of attacks without potentially blocking a legitimate request.
However, in the context of home routers, things change. Guests always asked for WiFi. Sure, I could isolate their access with guest WiFi feature, which only allows them to access the internet and not the other LAN devices. But how about other devices that I need to access like printers or an AirPlay speakers. Do I trust an old WiFi-capable printer? I certainly don't. Now to combat malicious traffic, we could leverage the so called threat intelligence.
Threat Intelligence provides us with information about potential threats (duh!). This could range from a traffic signature (like the body of an HTTP connection) to SSL fingerprint or IPs. In the next sections, we will go deeper about different options available.
Intrusion Detection/Prevention System (IDS/IPS)
In my old router, I used OPNsense. There, suricata is provided as both an Intrusion Detection System (IDS) and Intrusion Prevention System (IPS) systems. Suricata analyzes the traffic and matches it against a ruleset. If traffic matches a certain rule, then it will be logged and possibly also blocked.
However, with modern traffic increasingly encrypted, such system has a limited usage. Additionally, since the traffic must be matched against all rules, this option requires (relatively) high computing power and this requirement also increases with the number of rules used.
OpenWrt offers similar software called snort as IDS/IPS system. However, I decided to skip this option, due to the typical low CPU performance of most home routers and the fact that almost all my traffic are encrypted.
IP Blocking
The simplest way to block traffic is by blocking their IP. Unlike IDS/IPS which needed to parse the whole traffic, IP is already processed in the normal "routing". But how do we know which IP to block? Well this is where threat intelligence comes in. There are companies or groups (or individuals?) that tracks "bad IP" so that we can block them.
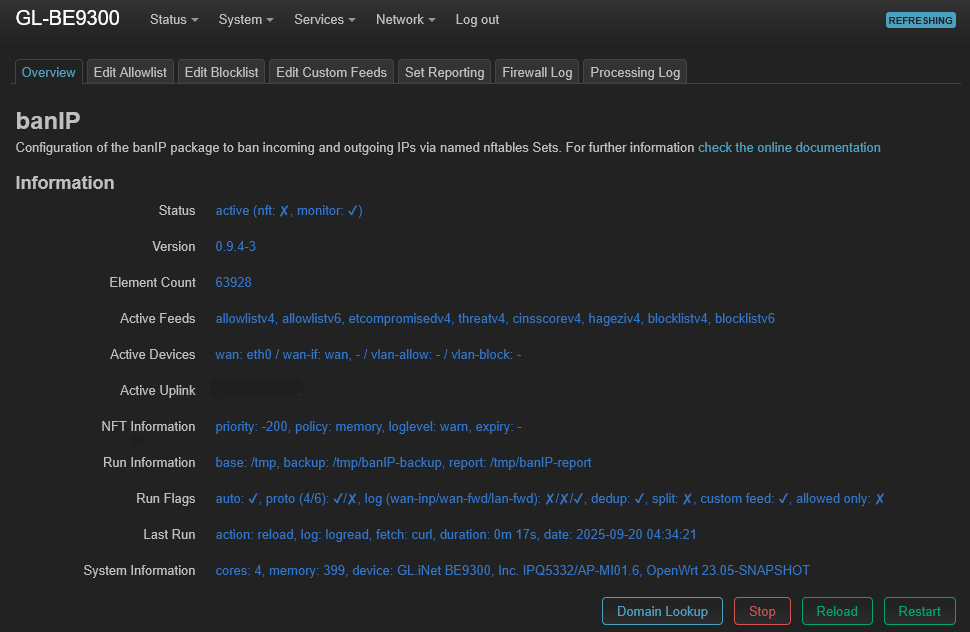
To use a blocking threat intelligence feed in OpenWrt, we can use the banip package and its LuCI frontend luci-app-banip. After downloading the packages, I just need to click a few settings in LuCI to enable it. The package banip provides some default feeds, but since I don't use the latest OpenWrt, my feeds was old and some of them didn't even exist anymore. No worries though, I can still set a custom threat intelligence feeds. I copy pasted some default feeds and added one from HAGEZI. The following is my custom feed list (/etc/banip/banip.custom.feeds).
{
"etcompromised":{
"url_4":"http://rules.emergingthreats.net/blockrules/compromised-ips.txt",
"rule_4":"/^(([0-9]{1,3}\\.){3}(1?[0-9][0-9]?|2[0-4][0-9]|25[0-5])(\\/(1?[0-9]|2?[0-9]|3?[0-2]))?)$/{printf \"%s,\\n\",$1}",
"descr":"ET compromised hosts"
},
"threat":{
"url_4":"https://rules.emergingthreats.net/fwrules/emerging-Block-IPs.txt",
"rule_4":"/^(([0-9]{1,3}\\.){3}(1?[0-9][0-9]?|2[0-4][0-9]|25[0-5])(\\/(1?[0-9]|2?[0-9]|3?[0-2]))?)$/{printf \"%s,\\n\",$1}",
"descr":"emerging threats"
},
"hagezi":{
"url_4":"https://raw.githubusercontent.com/hagezi/dns-blocklists/main/ips/tif.txt",
"rule_4":"/^(([0-9]{1,3}\\.){3}(1?[0-9][0-9]?|2[0-4][0-9]|25[0-5])(\\/(1?[0-9]|2?[0-9]|3?[0-2]))?)$/{printf \"%s,\\n\",$1}",
"descr":"HAGEZI IPs"
},
"cinsscore":{
"url_4":"https://cinsscore.com/list/ci-badguys.txt",
"rule_4":"/^(([0-9]{1,3}\\.){3}(1?[0-9][0-9]?|2[0-4][0-9]|25[0-5])(\\/(1?[0-9]|2?[0-9]|3?[0-2]))?)$/{printf \"%s,\\n\",$1}",
"descr":"suspicious attacker IPs"
}
}After turning on and manually checking if the banip works, we also need to download a new feed and I prefer do download new feed daily. To do this I need to create a new cronjob with the following command crontab -e and add this content 15 03 * * * service banip reload. In other Linux distribution, this cron is normally automatically applied, but in OpenWrt we need to restart (or maybe reload is enough?) the cron first with service cron restart.
Conclusion
I had my old OPNsense router with suricata enabled. Now that I've moved to OpenWrt, I still feel safe enough with the banip package and almost the same threat intelligence feeds with my old OPNsense router. Looking at the log, I block around 10k requests a day, of which only under 100 of them are actually trying to access open ports (80 and 443). I've used these threat intelligence feeds for a month now and it works great! Leave a comment down below if you have other feeds that I can use.

Member discussion